Even hackers wear (protective) masks, part 1
The leakage or theft of sensitive information constitutes a serious security breach or a form of cybercrime. Hence, it is not uncommon that security experts consider data exfiltration as one of the more representative targets of motivated cyber attackers [MITRE ATT&CK], [CYBER KILL-CHAIN].
In a series of articles – in the role of an independent pentester – we outline typical deficiencies in the design of information systems that (all too) often fail to provide sufficient ability to detect and prevent such attacks. In the first section, the issue of weak restrictions on egress communication in typical information systems of organisations is presented to the reader. The central part provides a description of more advanced malware technology that is based on the abuse of the perfectly legitimate and established DNS protocol (Domain Name Service), but enables complete control of the compromised system or, rather, the leakage of the data stored on it. The conclusion gives recommendations to enhance existing security mechanisms, so as to minimise the effect of established hacker techniques.
A simple test that is systematically performed in the client’s information system (e.g. as part of pentest or red teaming engagement) within the scope of reconnaissance is the test of restricting outbound communication. The latter is carried out in the direction from the user, e.g. a company employee or a home-based employee, towards the Internet. In the example below, we used Powershell. The tool is present by default in all modern versions of the MS Windows operating system and is, as such, (easily) accessible not only to users but also to a successful attacker or injected malicious code:
| 1.. 65535 | % {echo ((new-object Net.Sockets.TcpClient).Connect(“C2_IP“,$_)) “Port $_ is open!”} 2>$null |
With the use of a simple one-liner, we check the selection of open communication channels in the direction from the user to the Internet. One might question the true significance or sensibility of doing such a test. Attackers are nevertheless outside secured information environments, which is why their attempts are expected to be targeted in the opposite direction. Many independent studies and specialists in information security have warned of the predominant share of cyber-attacks of internal origin.
Typical components of such an attack are:
- persistence and
- command and control (C2) of the compromised system.
C2 technique [2] is based on the set-up of a reverse communication channel between the victim and the attacker’s command&control server and is usually the result of the launch of malicious code (e.g. by a user who clicks on a malicious attachment) or exploitation of a critical vulnerability of a running tool or application on a compromised system. A malicious reverse connection is established in the direction from the user towards the Internet, which makes it even harder to identify it and contain it in (at least) a seemingly legitimate communication between internal users and the worldwide web. Taking into account the predominant finding from security checks, i.e. that egress security policies of edge security devices are much laxer than ingress ones, the success of a C2 connection to the attacker’s server is more probable.
Let us consider at this point which egress communication channels are usually permitted in the edge security systems of organisations. In the wild, pentesters are exceptionally, rather than as a rule, faced with enhanced configurations in terms of security, where the selection of permitted employee communications is selectively restricted solely to the web (e.g. HTTP/HTTPS) and mail service (e.g. IPAM, MAPI, SMTP). These are considered to be the most widely established forms of communication and information exchange in business entities, which is why their existence is practically urgent.
Nevertheless, does the restriction of communication channels (to exclusively web and mail) suffice for efficient cyber defence? It turns out that well-established communication channels, particularly when they are additionally encrypted (e.g. HTTPS, IMAPS), also provide an ideal ground for masking malicious activities by more and more skilful cyber attackers. Another extreme phenomenon has also been noticed in which nominally “secure” protocols (e.g. HTTPS) are, knowingly and due to the questionable impact of inspection, not subject to in-depth analysis on dedicated security devices. We believe that to be entirely unjustified, which can be seen from another example. The activated protocol and application inspection of TCP/80 should undoubtedly (or unambiguously) recognise the lower “loud” attempt to set up a reverse command shell.
|
VICTIM [SIQ\mmesojednik]:
|
The captured traffic (use of the Wireshark tool) clearly shows the tunnelling of the command shell via TCP/80, which is ordinarily intended for web browsing (HTTP):
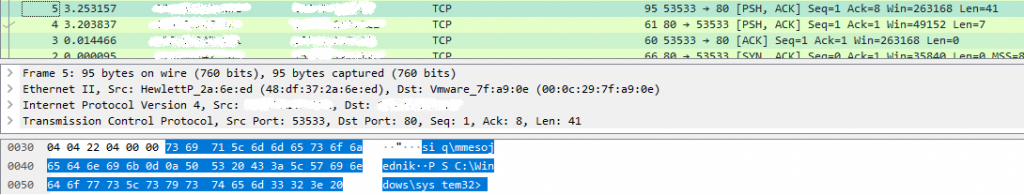
To that end, next-generation security solutions have an in-built ability to identify protocol and/or application deviations on random transport channels.
Organisations with an efficient defence strategy in place against the most advanced cyber-attacks carry out a similar inspection of any interaction with service users, independently of the use of:
- the transport protocol (TCP or UDP),
- transport ports (TCP/80, TCP/443) or
- additional layers of encryption (HTTP, HTTPS).
Remember, all of the above communication channels may be – in the event of weak protocol or application inspection – the attacker’s window of opportunity for undetectable:
- delivery of malicious code,
- its further spread and/or enhancement and
- leakage of sensitive information.
Pentesters rarely encounter information environments with an extremely selective egress security policy that would completely prevent the use of the mentioned techniques. And yet we are also prepared for extreme circumstances, where the pentesters’ (attackers’) interactions with external entities are not permitted or likely.
The second part (part 2) of the series of articles will show a more advanced technique to abuse the DNS protocol, the use of which has been considered indispensable by most organisations. On the other hand, its successful abuse provides the attacker with remote control, overall management and leakage of data even from environments with extremely conservative security policy in place. Stay tuned …