Information Security
Information Security Management Systems
The growing dependence on information technologies, openness of organizations, increasing importance of information in modern business and the desire to regulate and unify the field of information security within organizations are all reasons behind the birth of the ISO/IEC 27002 and ISO/IEC 27001 standards for information security management.
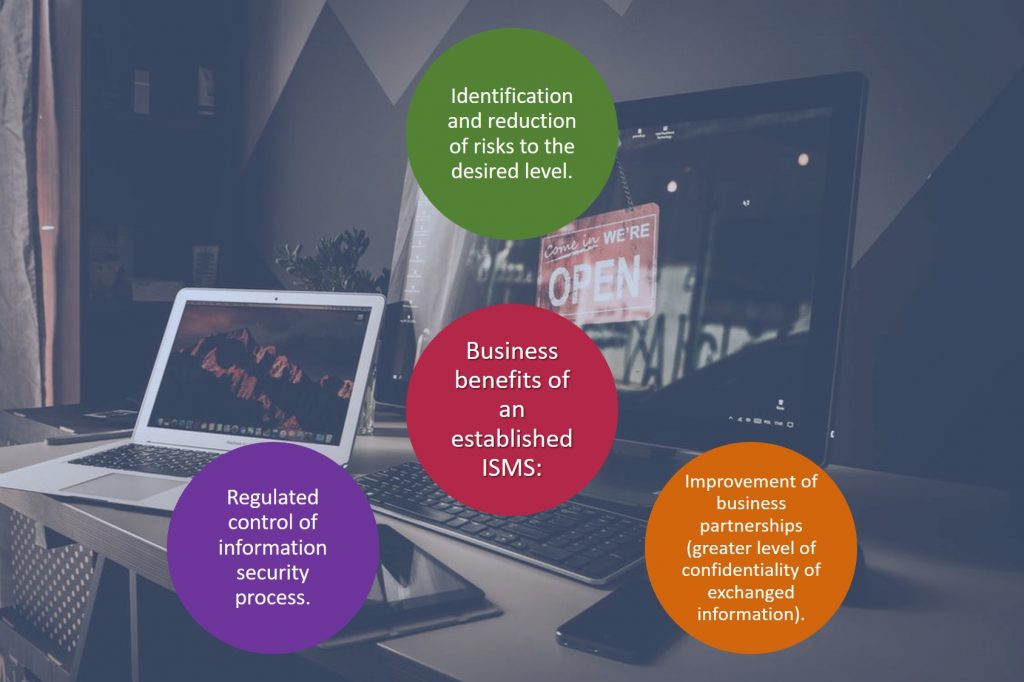
The standards are management tools which are independent of individual information technology solutions. They offer a comprehensive overview of information security in an organization’s operation. The assessment of information risks forms the basis for establishing the information security management system and is its main and fundamental characteristic.
The ISO/IEC 27002 offers a series of measures to control identified risks, which over the years and after having been applied by various organizations around the world have proven themselves as cases of best practice. The fourteen chapters of the standard provide descriptions of 114 controls for achieving 35 different objectives.
The ISO/IEC 27001 standard specifies the requirements an organization must meet in order to be granted a certificate. The requirements listed in Chapters 4, 5, 6, 7, 8, 9 and 10 must be taken into consideration without any exclusion and in full. Annex A of this standard provides a summary of 114 controls from the ISO/IEC 27002 standard. For each control not taken into consideration, an organization must state the reasons for its exclusion.
The standards are comprehensive in the sense of information security as they are not restricted to information technology and information in an electronic form but deal with information in any form and in any media. In this sense, many of the controls described are of a mere organizational nature and are not in any way related to technology (for example, classification of information, clear desk policy, physical security, description of information security in employment contracts).
Contact

- SIQ Ljubljana
- Mašera – Spasićeva ulica 10
- SI-1000 Ljubljana
- Janez Lemič
- Tel: +386 (0)1 4778 148
- janez.lemic@siq.si